The Trusted Device List continues to be one of the most misunderstood concepts in digital cinema. In a technology where a little bit of knowledge can be dangerous, the name invites misguided thoughts of centralized data and the means to block competition. This causes politicians to needlessly gravitate towards implementation of government policies and regulations.
The concept of a trusted device list is fundamentally sound. Content owners want to know that their content is played on valid, secure equipment. One way to guarantee this is to create a “revocation list,” containing the digital certificates of equipment that is no longer trusted. But in digital cinema, such a list could create all sorts of havoc. The very idea that a theatre system could be blacklisted by placing it on a revocation list met with an unfriendly reaction from the exhibition community. To prevent malicious behavior, revocation lists must be monitored and maintained by neutral parties. In practice, such neutral parties make their money off of certificate-related trust transactions. Even if a trusted neutral party existed, at worst, projection systems could be required to be online to play a movie (potentially leading to dark screens), and at best, no one is willing to pay for trust-related certificate transactions. Needless to say, there are no neutral parties in digital cinema, and so there are no revocation lists.
The issue of trust, however, is real. While engineers talk about security systems, they tend to forget that the ultimate authority of trust is a human being. The purpose of security systems is to minimize the number of people that must be trusted.
In current practice, trust is in the hands of multiple parties. The exhibitor, the equipment manufacturer, and the KDM Creator (the entity that creates a Key Delivery Message) all must be trusted. If there is a third party in between as a handler of security processes, then that entity must be trusted, too. As digital cinema expands globally, studios would like to not have to trust exhibition personnel for the secure handling of their content. They would rather that the systems onsite handle trust in terms of content security, and the exhibitors be left to handle business.
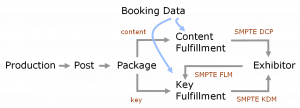
In understanding the trust issues, we must start with how things are done today. Trust begins with the manufacturer of the equipment, who maintains a list of equipment serial numbers and associated digital certificates. The exhibitor provides a list of serial numbers of active equipment, and a 3rd party marries the serial number with a manufacturer-provided certificate. The 3rd party could be the system integrator, a separate service provider, or a KDM Creator, or a combination of these.
The most sensitive activity in the digital cinema security chain is that of the KDM Creator. Once a KDM is created, the movie can be decrypted on the device to which the KDM is targeted. Without a matching KDM, the movie cannot be decrypted on a device. Should a KDM be created for a device that is not intended to play the movie, or a device that is no longer trusted, then a breach of trust has occurred. The KDM Creator is hired by the content owner, so a trusted relationship always exists between these two entities.
In order for a KDM to be created, the target device’s digital cinema certificate must be known. This requires that the KDM Creator possess trusted information obtained from both exhibitor and equipment manufacturer. The KDM Creator also has a degree of responsibility in making trusted decisions. If the movie does not play because of an incorrect KDM, it is the KDM Creator that must respond appropriately. Thus, in practice, it is the KDM Creator who must maintain a list of certificates for each cinema. It is one of its responsibilities in its role as a trusted service provider to the content owner.
Any weakness in the security chain is due to the number of entities that must be trusted. Ideally, only the KDM Creator will need to be trusted, and not the manufacturer or exhibitor. It is not possible, however, to eliminate the manufacturer as a trusted party, as it is the source of digital certificate information. But it is possible to eliminate the exhibitor as a trusted party by automating the communication of certificates from the cinema to the KDM Creator.
Tools have already been created to enable this important step. It is the purpose of the standardized Facility List Message, or FLM, to carry digital equipment certificate information back to KDM Creators as part of an automated process.
Even with the FLM in place, the trust chain is not perfect. The KDM Creator must know when a particular device is removed from service or no longer valid. It is assumed that the manufacturer will remain responsible for tracking this information and appropriately updating its database.
The question of how 3rd parties play in the trust chain is often raised. Deployment entities such as AAM, Cinedigm, DCIP, and XDC all track the installation and movement of equipment in cinemas that they monitor. These are not neutral entities, as they have a stake in the exhibition of a movie in order to collect VPFs. But as deployment entities, they each have a business relationship with their exhibitors and with the studios whose content is booked at those sites, and so are trusted parties.
What doesn’t fit well in the trust chain is government-sponsored certificate handlers. Without a business relationship to the main parties in the trust chain, there is no incentive for such entities to be responsive to the needs of studios and exhibitors, both business and security-wise.
This long walk through the digital cinema trust chain is hopefully instructive in a number of ways. It educates the steps required to maintain trust. It demonstrates where responsibilities lie. And it shows why automation of certificate handling in the cinema is necessary to improve the trust chain for global expansion.
NATO’s Digital Cinema Requirements identifies the Data and Key Management System, or DKMS, as the component providing the automated management of certificates in the cinema. SMPTE standardized the FLM for open exchange of certificate information. Unfortunately, none of this has been put to work as yet. Notably, DCIP will break ground by requiring that KDM Creators make use of DCIP-supplied FLMs. In turn, DCIP requires that its exhibitor systems generate FLMs at each site. The next step, however, is for DKMS-like devices to proliferate globally.